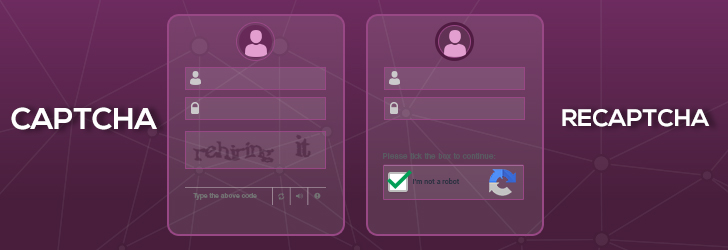
With hacking attacks going to the next level, most websites have become more vigilant to shield every possible cyber-attack. Captcha is something that has been around for some time now and several top websites incorporate captcha.
Captcha is a challenge-response test provided over the website. This is used to determine if the user is a human or an automated bot. Captcha was first formed in 1997 and was officially introduced in 2003 by John Langford, Nicholas Hopper, Luis von Ahn, and Manuel Blum.
[..]
Read more...