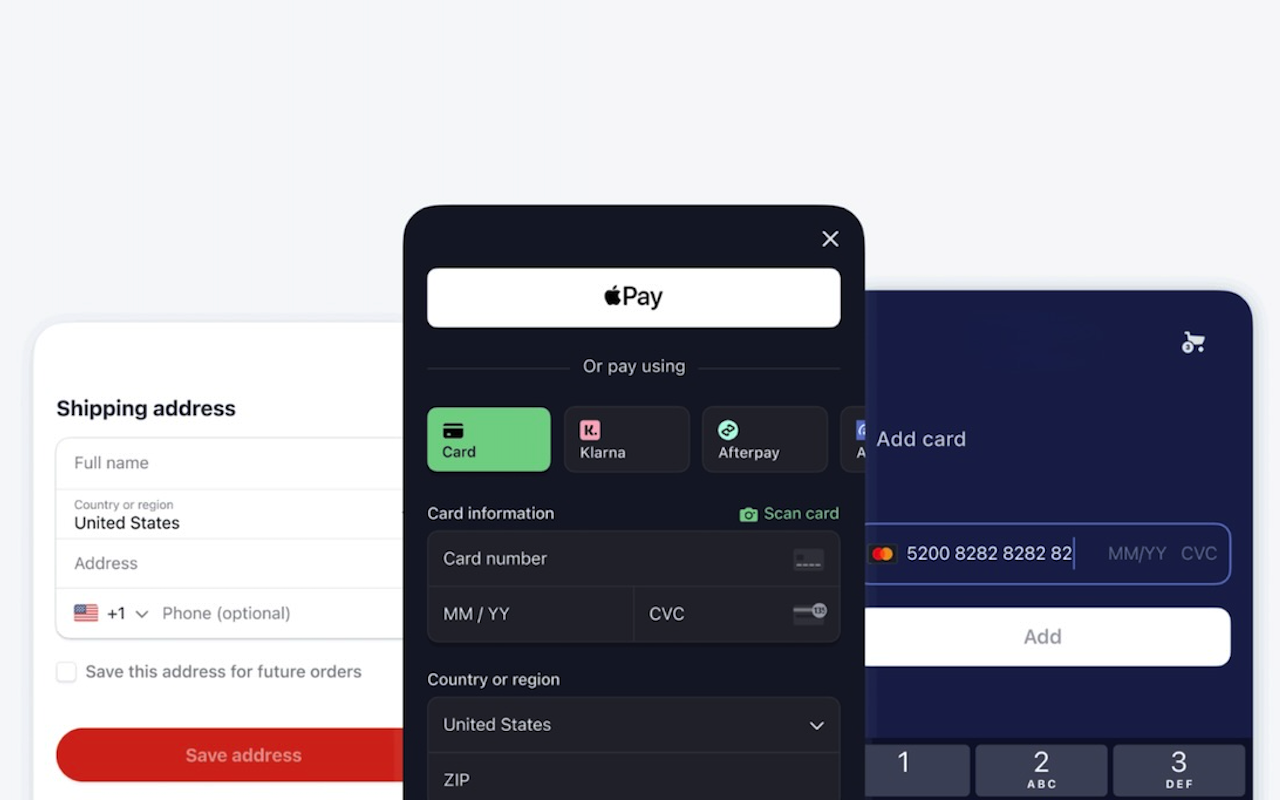
As the subscription economy continues to grow, more developers are looking beyond the native billing systems of Apple’s App Store and Google Play. While these ecosystems offer seamless integration and user trust, they come with trade-offs, most notably high transaction fees and limited control over customer experience. This has led to the rise of external, third-party billing providers like Stripe, Paddle, and Braintree.
[..]
Read more...