asdasd
Blog Category

An IP stresser is a network load testing tool designed to evaluate the stability and performance of a server or online service under heavy traffic. Organizations use IP stressers to simulate peak loads, identify weak points, and ensure that a website or network can handle surges in requests without downtime.
Have you ever experienced a situation where your site is slow to crawl on a regular traffic day? That could be a silent warning of a DDoS attack on your website. While most teams have strong firewalls and server logs to protect their backend, there is no way to discover the front-end issues.

With our dependence on the Internet growing each day, businesses face a significant threat from DDoS (Distributed Denial of Service) attacks. DDoS is a type of cyberattack where multiple compromised systems, often referred to as a botnet, are used to flood a target website with an overwhelming volume of malicious traffic. The goal of DDoS attacks is to overwhelm the target server to prevent normal operation, disrupting the business. Website owners must implement effective strategies to mitigate DDoS attacks.

Most of us use our Google Homes, smartwatches, security cameras, and other handy gadgets on a daily basis. The Internet has undoubtedly made our lives ten times easier than before. However, the thing that makes these devices so convenient and easy to use is the same thing that makes them most vulnerable to malicious cyberattacks.

A reverse proxy is a server that sits in front of the webserver, intercepts the request, and either respond to the client with a response from its cache or forward the request to the origin server. A reverse proxy is used to protect the web servers from DDoS attacks, distribute load amongst multiple servers, and utilize its cache to serve static contents without sending requests to the origin server. No client will communicate directly with the server, and the server's IP address will not be revealed to the public.
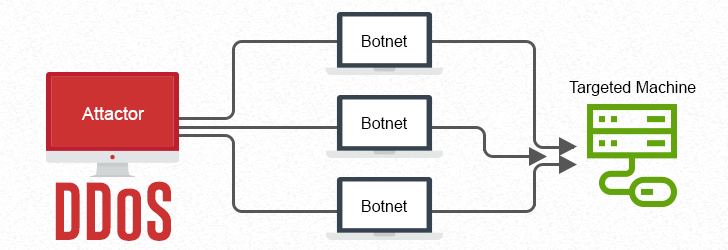
A denial of service (DoS) attack is an explicit attempt made by an attacker to make victim's Internet resources unavailable to its intended audiences. The DoS attack is usually carried out by one machine connected to the Internet by exploiting known UDP and TCP vulnerabilities.

Wordpress is one of the most popular CMS platform available today with over 75 million websites powered by it. The popularity comes with risks as vulnerabilities and weakness of such platform will be shared amongst hackers and script kiddies, and automated bots will be searching for websites built on Wordpress platform.

Given the fact that a DDoS attack can bring down any computer system in spite of the advanced hardware setup, it is essential to do some periodic checks in order to detect the possibility of a DDoS attack. Here are some essential ways to prevent and mitigate a DDoS attack.

One of our sister website hosted on cloud server was recently hit by a 9Mbps DDoS, and the apache web server ran out of memory and crashed. The attack lasted more than 2-months with no known reason. We've taken a number of mitigation steps including installation of mod_security with mod_evasive, APF, BFD, DDoS Deflate and Rootkit and Traffic Control, but none came to rescue. Use of Linux provided WAF will mitigate the DDoS to the extent where CPU, Memory and Bandwidth are allowed; and in our case a single CentOS server with 4GB RAM wasn't sufficient to mitigate DDoS.
